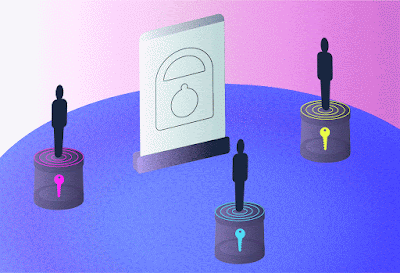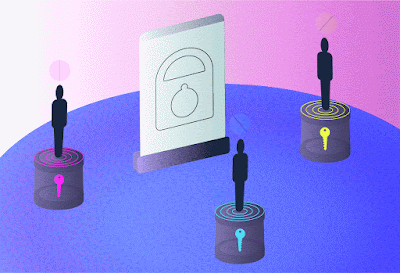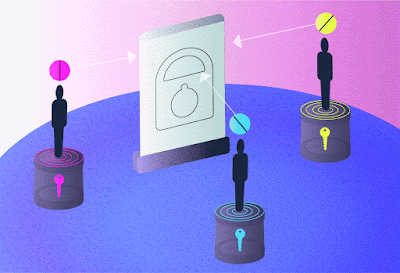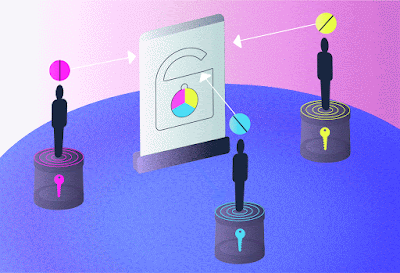
High-dimensional quantum transport enabled by nonlinear detection. In our concept, information is encoded on a coherent source and overlapped with a single photon from an entangled pair in a nonlinear crystal for up-conversion by sum frequency generation, the latter acting as a nonlinear spatial mode detector. The bright source is necessary to achieve the efficiency required for nonlinear detection. Information and photons flow in opposite directions: one of [the] Bob’s entangled photons is sent to Alice and has no information, while a measurement on the other in coincidence with the upconverted photon establishes the transport of information across the quantum link. Alice need not know this information for the process to work, while the nonlinearity allows the state to be arbitrary and unknown dimension and basis. Credit: Nature Communications (2023). DOI: 10.1038/s41467-023-43949-x
Topics: Applied Physics, Computer Science, Cryptography, Cybersecurity, Quantum Computers, Quantum Mechanics, Quantum Optics
Nature Communications published research by an international team from Wits and ICFO- The Institute of Photonic Sciences, which demonstrates the teleportation-like transport of "patterns" of light—this is the first approach that can transport images across a network without physically sending the image and a crucial step towards realizing a quantum network for high-dimensional entangled states.
Quantum communication over long distances is integral to information security and has been demonstrated with two-dimensional states (qubits) over very long distances between satellites. This may seem enough if we compare it with its classical counterpart, i.e., sending bits that can be encoded in 1s (signal) and 0s (no signal), one at a time.
However, quantum optics allow us to increase the alphabet and to securely describe more complex systems in a single shot, such as a unique fingerprint or a face.
"Traditionally, two communicating parties physically send the information from one to the other, even in the quantum realm," says Prof. Andrew Forbes, the lead PI from Wits University.
"Now, it is possible to teleport information so that it never physically travels across the connection—a 'Star Trek' technology made real." Unfortunately, teleportation has so far only been demonstrated with three-dimensional states (imagine a three-pixel image); therefore, additional entangled photons are needed to reach higher dimensions.
'Teleporting' images across a network securely using only light, Wits University, Phys.org.